Hi,
I have Plesk Obsidian 18.0.34 on Windows Server 2019.
I found a shell file (.aspx shell) on a web site.
I moved it to another web site and looked it to see its functions and access limits. But I am shocked when I see results. I can access root folder (C:\) of disk and can access many places. Some directories couldn't be accessed (C:\Inetpub)
But I can access many directories.
How this file can access to folders beyond the web site httpdocs folders? Is it normal ? If not, how can I fix this security vulnerability?
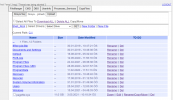
I have Plesk Obsidian 18.0.34 on Windows Server 2019.
I found a shell file (.aspx shell) on a web site.
I moved it to another web site and looked it to see its functions and access limits. But I am shocked when I see results. I can access root folder (C:\) of disk and can access many places. Some directories couldn't be accessed (C:\Inetpub)
But I can access many directories.
How this file can access to folders beyond the web site httpdocs folders? Is it normal ? If not, how can I fix this security vulnerability?

