- Server operating system version
- centos 7
- Plesk version and microupdate number
- 18.0.50
Good afternoon everyone.
I wanted to ask you about the following.
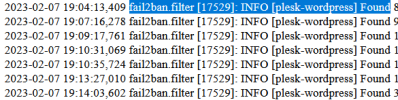
Reviewing the Firewall log, I have seen that I had many SSH attacks, which I have cut from Raid.
But still they continue to appear this type of messages and I don't know what they are, and I don't know how to block them.
You can tell me what I should do.
Thank you.
fail2ban.filter [17529]: INFO [plesk-wordpress] Found xxx.xxx.xxx.xxx
From several IP addresses
I wanted to ask you about the following.
Reviewing the Firewall log, I have seen that I had many SSH attacks, which I have cut from Raid.
But still they continue to appear this type of messages and I don't know what they are, and I don't know how to block them.
You can tell me what I should do.
Thank you.
fail2ban.filter [17529]: INFO [plesk-wordpress] Found xxx.xxx.xxx.xxx
From several IP addresses