- Server operating system version
- Debian
- Plesk version and microupdate number
- 18.0.55
This server has had an infected hosting which created these files and ran that command using the FTP user and there was no way to stop it, every reboot and change of ftp data... was re-run
that hosting no longer has a web site only mail . So in theory we thought it was fixed but NO, now run this with user 10007
I search xmri no longer shows me any files because the infected website has NO website or place to upload files or infected files... any ideas ?
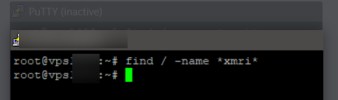
that hosting no longer has a web site only mail . So in theory we thought it was fixed but NO, now run this with user 10007
I search xmri no longer shows me any files because the infected website has NO website or place to upload files or infected files... any ideas ?


